
A Hardware Security Module (HSM) is a physical device that provides an additional layer of security to protect sensitive data. This device is used to provide cryptographic keys for critical functions such as encryption, decryption, and authentication for use by applications, identities, and databases. HSM generates and manages cryptographic keys and secures digital identities. As a result, HSM can become a pillar of trust for digital data protection. HSM is always needed when cryptographic keys in critical infrastructure need to be protected from software and hardware attacks.
These devices can be plug-in cards or embedded in other hardware, including smart cards, devices, and other external devices. They can be connected to a network server or used offline as a standalone device. They are also available as a cloud service.
Companies use HSM to keep cryptographic functions related to transactions, identities, and applications separate from regular operations and to control access to these functions. For example, companies may use HSMs to protect trade secrets or intellectual property by ensuring that only authorized individuals have access to the HSM to perform cryptographic key transfers.

General Purpose HSM:
A General Purpose HSM is a hardened, tamper-resistant piece of hardware that strengthens encryption practices by generating keys, encrypting and decrypting data, and generating and verifying digital signatures. Some hardware security modules (HSM) are certified for various FIPS 140-2 levels. General Purpose HSM is used to Meet established and emerging cybersecurity regulatory standards, to achieve a higher level of Data Security and trust, and to maintain a high level of service and business flexibility.
General Purpose HSM is used for general operation, use-cases details are given below:
- PKI Signing & Validation
- IOT
- Code Signing
- SSL/TLS
- Blockchain
- eIDAS
- BYOK/HYOK
- Database Encryption
- Secure Manufacturing
- Document Signing
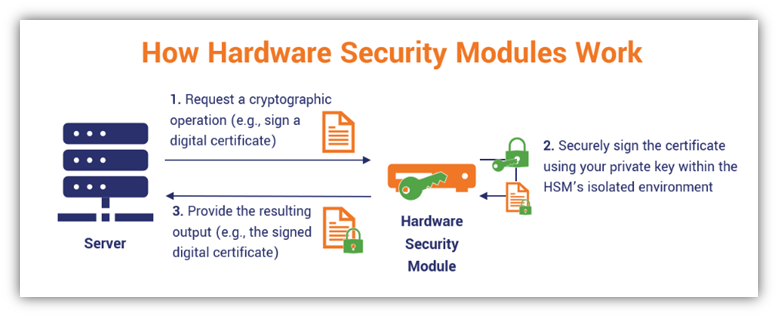
How Hardware Security Modules Work?
Payment HSM:
Payment HSM is hardened, tamper-resistant hardware used primarily by the retail banking industry to provide a high level of security for cryptographic keys and customer PINs used during magnetic stripe and EMV card issuance chips (and equivalent for mobile applications) and the following Process payment transactions with credit and debit cards. Payment HSMs typically provide exclusive cryptographic support for all major card scheme payment applications and undergo strict independent hardware certification against global schemes such as FIPS 140-2, PCI HSM, and other additional regional security requirements.
Payment HSM is used for Extra Protection. Use case details are given below:
- Issuing Payment credentials – cards, mobile secure elements, wearables, connected devices, and host card emulation (HCE) applications
- PIN routing
- Point-to-point encryption (P2PE)
- Security tokenization (for PCI DSS compliance)
- EMV payment tokenization
- Card and mobile payment authorization
- POS, mPOS, and SPoC key management
- PIN and EMV cryptogram validation
- Remote key loading
To Know more about HSM or for any query you can contact us at +91-9818221255 or write us at info@anveshvision.com.
hsm
